Taking Control: A Security Expert Unveils Drone Vulnerability
Security Expert shows how easy it is to "Take Over" ...
BY ML SHAW
A security expert (SSHad0w) recently demonstrated the ease of hijacking a DJI Tello drone, highlighting critical vulnerabilities in drone software. This exercise no doubt adds to the public's perception and evolution of drone technology. The potential for these devices to be commandeered by unauthorized parties raises the risks to using them.
Drones, now the subject of military innovation and application, have saturated into civilian life, becoming tools of the trade for photography, recreation, and increasingly, commerce. Among these, the DJI Tello has distinguished itself as a favorite for its user-friendliness and versatility. However, beneath the surface of this widespread adoption lies a stark vulnerability, one that could potentially pivot these devices from instruments of convenience to intrusion.
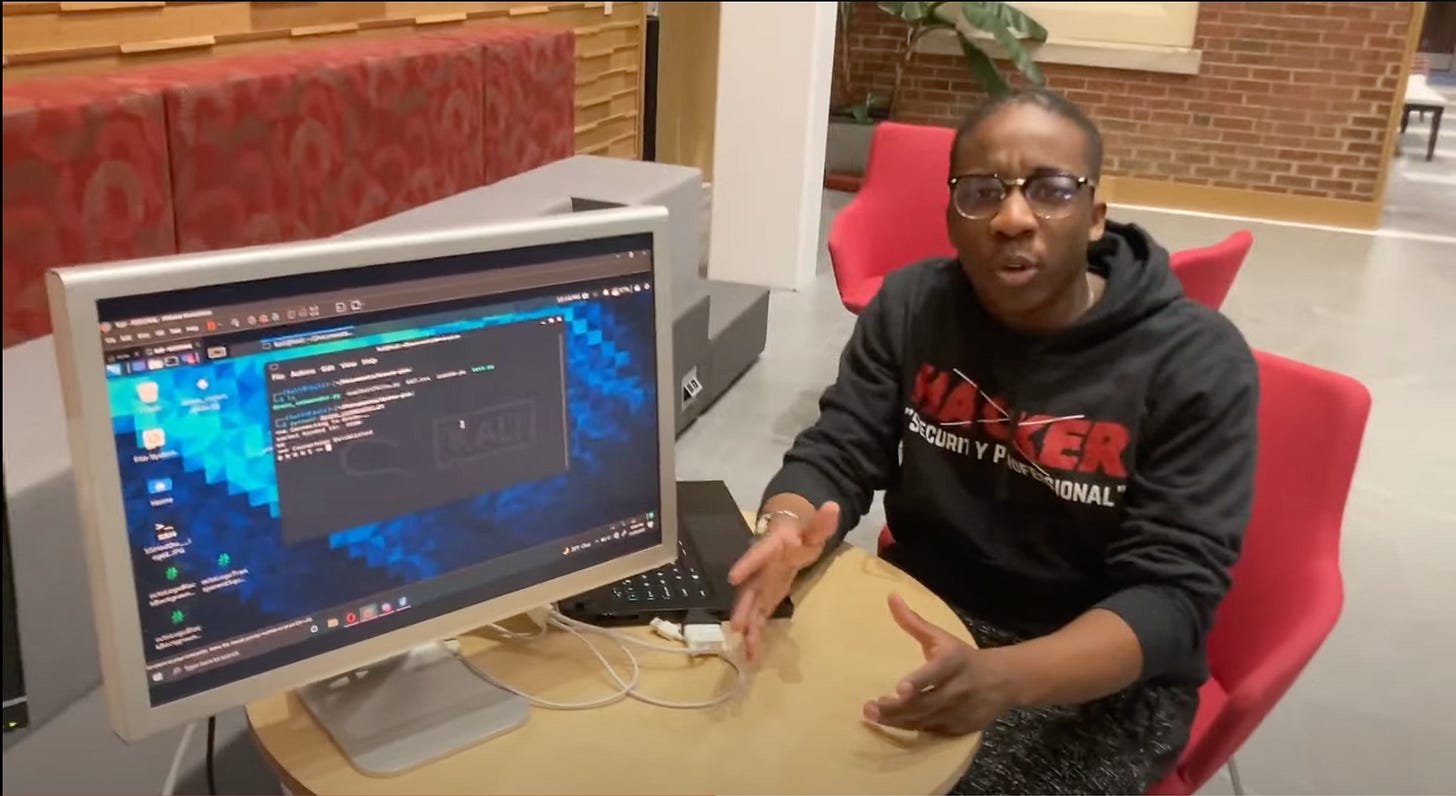
The crux of this vulnerability was laid bare in a straightforward yet easy demonstration. A security expert, equipped with nothing more than the drone's standard app and a custom script named droneCommander.py, unveiled how effortlessly the Tello drone could be manipulated. By exploiting the drone's Software Development Kit (SDK), the expert showed the ability to sever the drone's camera feed, signaling the loss of control by the rightful owner.
The demonstration revealed the drone responded to a series of unauthorized commands, performing maneuvers and exposing system information such as battery life at the hacker's whim. This commandeering not only exposed the ease with which these devices can be hijacked but also the starling implications of such vulnerabilities in a world increasingly reliant on drone use.
The event serves as a call to both manufacturers and users, emphasizing the pressing need for stringent security measures in the design and operation of drones. The simplicity of the takeover, enabled by rudimentary Wi-Fi access and the inherent capabilities of the SDK, highlights the critical importance of safeguarding these devices against unauthorized access.
The military use of civilian drones in war is now common. Especially in Ukraine and Israel. Ukraine's innovative drone use for reconnaissance and improvised bombing runs highlights a strategic shift. Similarly, Israel's deployment for surveillance and targeted strikes redefines military tactics. This evolution in warfare, where drones play a central role, emphasizes the digital battleground's significance.
The horizon of drone technology has expanded from the mundane to the deadly, incorporating everything from delivery services to emergency response. This “Take Over” exercise underscores an essential truth: in the rush towards innovation, security must not be left behind.
It calls for a collective push for robust protections, ensuring that drones remain tools of progress, not peril. This episode, while a stark warning, also offers an opportunity—a chance to reinforce the security frameworks that underpin this technology, safeguarding the skyways of tomorrow or not.
SSHad0w’s Demonstration: